ICS/SCADA Vulnerability Management
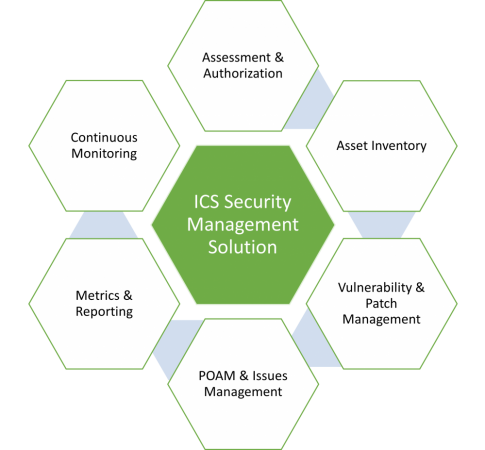
The world has seen a staggering increase in Industry Control Systems (ICS) Supervisory Control and Data Acquisition (SCADA) attacks in the past decade with no sign of slowing down in the near future.
The ICS/SCADA security and compliance landscape introduces a new dimension of risks that can have significant ramifications that span from loss of resources, financial losses, damage to brand reputation, and potentially loss of human life.
Operation Technology teams in key industries such as the electric power grid, power generation, water and sewage systems, the transportation industry, oil and natural gas pipelines, automated manufacturing, chemical plants, and many others utilize Industrial Control Systems (ICS) and Supervisory Control and Data Acquisition (SCADA) systems.